KeyGrabber WIFI Air (by KeyDemon)
Reviewed Oct 2019 by Jon Munsey
So what have we here, a hardware device that fits in between a USB keyboard and the computer it is plugged into. It then logs keystrokes, with some interesting methods for covertly getting the keylog files off it once installed.
Surveillance is an interesting part of our world and as I am in partnership with various Detective Agencies, they often have a need for cool toys to catch a crook !
I bought this device on Ebay about six months ago and never got round to using it, I kept it in the same drawer as a certain dongle that went faulty a while back :) so this is not a paid or sponsored review.
3. About the vendor
KeyDemon have been around on the web since 2009, so they are certainly not new to this market. It seems their distrubutor for europe is "Electroware", based in Poland. It also looks like they are a Chinese based manufacturer, whether or not they are the original developers of the software inside their devices, or these are knock-off, who knows.
UPDATE: It seems like quite a lot of Keyloggers in all shapes and sizes are using the same microcode as the KeyDemon products, so someone ripped off someone, somewhere.
4. Feature Overview
As you can see below (click to enlarge), the Keygrabber Air USB has some interesting features, most notably;
- Records keystokes with a 16MB Memory capacity.
- Can upload keylogs via FTP or Email.
- Can be directly accessed via WIFI to directly download keylogs.
- Live streaming of keystrokes if required.
- Offers NTP time sychonisation (Gotcha! coming up).
This device is not suitable for laptops (as they have a built in keyboard), it also "apparently" does not work on Apple computers, according to the user manual.
Interesting as a PC keyboard works on a an Apple computer and an Apple keyboard works on an Apple device, if a client was paying I would be looking at the scan codes the keyboard is sending down the USB bus with a sniffer - but they aren't, so I won't :)
For the "Machiavelians" (roars with laughter uncontrollably!!) armchair experts, yes I know that the vendor maybe talking about the ye-olde ADB keyboards from yesteryear, but KeyDemon have a specific USB version for Apple listed on their website - so I'm confused!.
Quick Quiz: So what does ADB stand for then ? Kudos if you know without Googling it. First one to comment with the correct answer before the closing date (see bottom of page) wins an all expenses paid trip (thats hotel, meals, spending money £1000/$1000 per day and flights from anywhere in the world) to Scunthorpe young offenders institution.
Pro Tip: I could not resist it, ok, so the reason they have a specific MAC version is that some older USB Apple Keyboards use the USB 1.1 specification, which causes issues, I found this (which relates to another vendors product, not this one being reviewed) which neatly explains it;
5. Further Resources & Reading
The manual for the KeyGrabber is very short, but surprisingly concise - so it tells you all you need to know. You can download it in .PDF form here or take a look below/
The manual is your usual Chinese to English translation, its not bad, and at this price point, who are we to complain ?
If you are not familliar with FTP, NTP, SMTP, SSID's and the like, then you won't be up and running with the advanced features out of the box, those will require some Googling. However if you just want to start logging keys (Gotcha! - see the Using The Product section) you are good to go.
6. Pricing, Licencing and Renewal
Pricing:
£15.45/$19.99/€17.90 plus postage & taxes will get you one of these delivered to your door.
Thats a very cheap price, considering what you are going to charge your client for doing this sort of work. You can spend more money, but the microcontroller and its code, will more than likely be the same or fairly close to what is inside the KeyGrabber.
Licence & Renewal:
There is no licence for this product, you buy it and it is yours to use until it bites the dust and ends up in your local landfill, so no renewal either.
7. Purchasing process
So I purchased mine from Ebay at this link, but this may expire by the time you read this, so here is the main vendors website.
It took a few days to arrive, but as the postage was a paltry £3.99/$3/€3.2 I was not complaining for international shipping from Poland.
For a size comparison to a regular USB memory stick, below we can see this thing is tiny! Apparently billed as the smallest in the world.
The build quality looks ok nothing is loose or wiggles around, the device is also unmarked and has no serial numbers, branding or any other marks that would arouse supicion.
9. Installation & Uninstallation
There is no software to install with this little beasty, it is plug and play, no drivers to install, nothing, zip.
10. Initial Impressions - First run
So plugging the KeyGrabber into my test machine, I'm using an old Windows 7 laptop here that I use for diagnostics over ODB on my car, its essentially an old netbook which I've used a home for eons which has been repurposed.
More on why I am using this machine later, but lets take a look at the device manager and see whats going on.
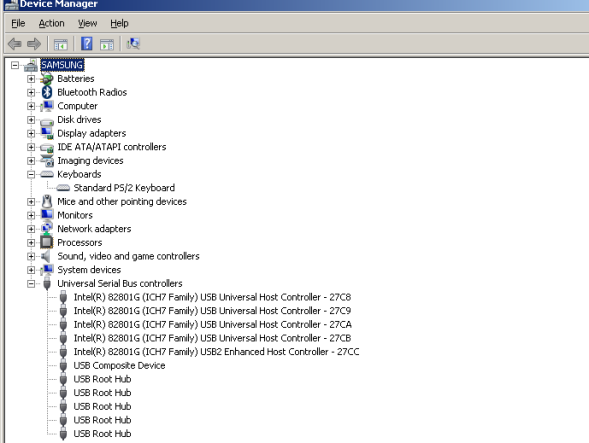
This is what we see in the device manager before we start, the keyboard listed is the internal one, so nothing unusual here;
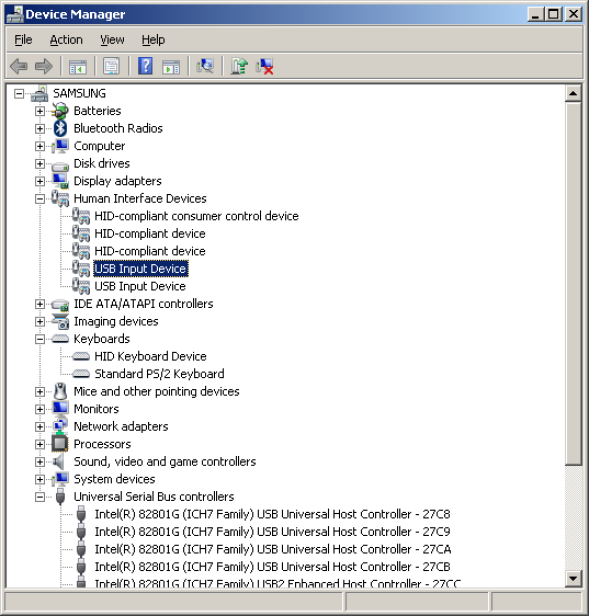
When we plug in the keyboard to the device, the Windows "plug and faff about" system comes to life and we now have an additional keyboard listed and plenty of HiD's (see below). This is going to generate events in the event log and such, especially so if you plug it into a different USB port when you replug the keyboard, so watch that.
None of this will be suspicious to the user as if they are using a USB keyboard, then this will all be completley normal if they come here and look.
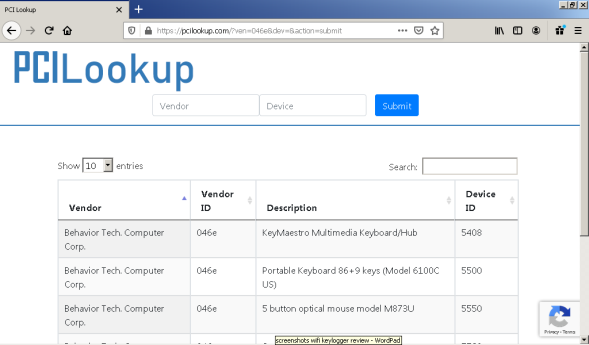
Examining all of those HiD's and the secondary keyboard entry for a dodgy PCI Hardware device ID that the sneaky ones of you will Google to detect the device won't help you out - they all relate to the keyboard.
A quick look in the setup.api.dev.log (that name keeps getting longer) also shows zero activity when the KeyGrabber was plugged in with no keyboard attached, and when the keyboard was attached, the only entries in the log file relate to that keyboard only.
So what we have here is a clever pass through device that seems to be completely invisible to the machine - well at least at the level of detail I am going into - way more than your average I.T guy who would poke around on his machine.
So far so good !
Being the uber geek that I am, I monitored file, registry and TCIP connections during the first time plug in of this device, as you can see below (click to enlarge), I don't trust anything, so I wanted to see what this thing was going to do when plugged into my machine.
Was it going to install some malware that sends the keywords captured off to China (and yes, I've investigated a case where that happened! - millions of dollars of cancer research stolen), or was it going to switch on my webcam and video me (man, that even makes me shudder *grin*).
I didn't see anything untoward or malicious at all, what you see here is a text book installation of a HiD device (the keyboard) and nothing else happened that was unexpected. Obviously this is a super short term test and naughtiness may take place at other intervals.
If you fancy reading about the Human Interface Device protocol and specification, take a look here.
Perhaps we will see something interesting when we hook this thing up to the internet and get it to E-Mail and upload logs via FTP!
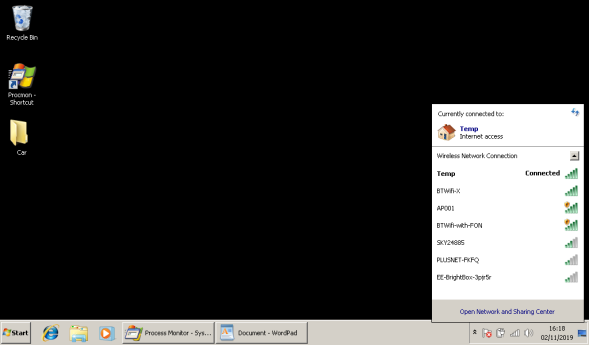
So, now this device is connected up to my test machine, lets have a look at the Wifi side of things.
As we can see below, Windows is detecting a WIFI network AP001, this is KeyGrabber's built in WIFI making itself available for intial configuration;
Obviously you need to configure the KeyGrabber, before you plug it into your target machine, otherwise you have just left a nice tit-bit (does that translate from British English ?), ok a "bread crumb" for anyone who is looking for this thing. It stores the config on its internal flash RAM.
Connecting to this network and accessing 192.168.1.5 takes you to the devices Admin console as you can see below;
The first thing needed is to change the SSID of the system to something less conspicious, so lets choose WIFILOGGER. I'm kidding around here, don't set it to that, my tip is look at the WIFI networks in the vicinity and name it in a similar way in an attempt to blend in, but you really don't want this thing to be transmitting when deployed.
There are a number of options here, you really need to enable "Hide SSID" so that this device does not appear to the target machine's WIFI adapter or anything nearby (such as the targets phone, tablet etc..).
You can still connect to the KeyGrabber, simply manually create a network connection and type in the SSID and password.
This keeps things extremely simple and once set up like this, chances of detection are very low.
Feature request - This admin page needs to be password protected, so that if you are rumbled, there is no way to access the device to see what it does, or access the logs it contains.
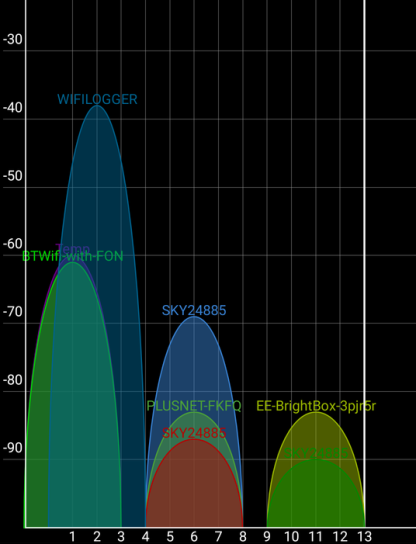
WIFI Signal:
Taking a look at the wifi spectrum, in the 2.4GHZ range where the KeyGrabber operates, we can see it pumps out a strong signal at close range, I didn't try this over any distance, but from these numbers I would imagine you would easily be able to sit outside a property or office in a car and connect without range being an issue.
ProTip: 2.4Ghz technology is old school and is essentially the 802.x "54g" standard in this implementation, this particular frequency is great for distance, but not so good at punching through solid objects, such as walls or anything reinforced with steel girders or mesh. Had this been a 5Ghz device, opeating on the current "a/c" standard, then you would have had less range and better pentration through walls - worth considering when deciding which standard to use on a target computer.
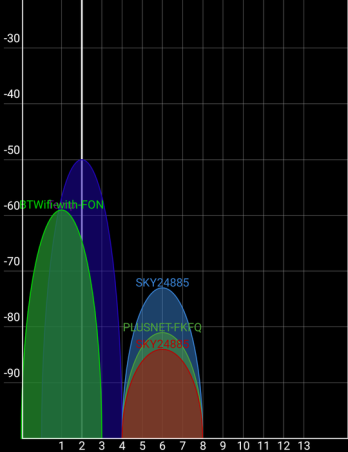
Turning off the SSID broadcast now semi anonymises our keylogger (blue signal with white line through below), which is exactly what is needed !
If you wish to use advanced features such as FTP, E-Mail and NTP, then you need to use WIFI Client mode;
This essentially connects the KeyGrabber to a WIFI network that is within range of the target machine.
If there is not one, perhaps think about setting up one in the room next door, or even a mobile/cell phone hotspot set up on a phone in your car in the car park outside!
Obviously connecting a £20/$20 network device running code which you know nothing about, to a clients network, is perhaps not the best idea in the world, but hey, I'm not your boss.
Most of the "Save" buttons in the web GUI are hit and miss, meaning you click them to save and then are unsure as to whether those changes have been saved.
What is really happening here is the micro-controller in the KeyGrabber is rebooting (like your router used to when you applied changes) and there is no pretty "please wait rebooting" or other form of progress bar. If you remember to click save and then wait about 60 seconds, you should be good to go.
This worked a treat for me, as long as the machine was powered on it connected to the Internet via a WIFI connection to my router. I don't know if this would connect using SFTP which would be the sensible way to send out keystrokes, but you can change the port number, so that is a maybe!
I examined the traffic and did not see anything straying off to where it should not go, but you pays your money and takes your chance here.
Email Log Transmission:
Setting up the Email method of transmission is also very simple and done from the web interface. Remember that the attachment limit is somewhere around 25MB for a Gmail attachment, going over that amount and your log files won't reach you.
You can find the exact limits by reading the Forensic Email Extractor review!
This also worked well, I had to enable the "allow less secure devices to connect" option on the test Gmail account I used, but once done, the key logs came in no problem.
11c. Using The Device - USB Storage Mode
Its possible to connect to the KeyGrabber by just pressing K B and S at the same time, this causes the USB device to reboot into Mass Storage mode. It then appears as a removable drive and you can access the LOG.TXT file directly from any Windows or Apple computer.
From this we can see that there is no security protecting the file, nor is there any fancy compression to allow for very long deployments.
Gotcha! You will need to ensure that you enable "Log Special Keys" otherwise you wont see keys such as CTRL, ALT or the Windows Key - which may be important to your investigation.
Gotcha! Wow, two in a row, you also cant set the time or date on the device, unless you give the device some form of internet connectivity (covered elsewhere in the review). As long as you note the time in the log file at installation, you can translate the time easily to the correct local time. You also have to factor in that when the computer the device is connected to is powered off, the clock will reset back to 12:00 01/01/2000. The log file is written to sequentially, so even after a power down, the log file is still chronologically recorded and the most recent keystrokes are appended to the end of the file.
This is perhaps an oversight by KeyGrabbers developers, but I think it is down to the fact that there is no room inside the device for a real time clock or battery to power it when the device is without power (when the computer it is plugged into is powered off as an example).
There are other versions of the device available that do have a real time battery backed clock (see the Alternative Products section), but these don't come with WIFI connectivity of any kind. So you need to pick the correct features for your application.
I did not notice any issues with the actual logging of keystrokes (they were all there - even when the WIFI signal had shut down), so this is not a total disaster, just a right PITA when you are standing in the corridor outside of a mob bosse's office, trying to download the key stroke log file.
There are no bug fixes or updates available for this product, it seems that the device has no re-writeable firmware - or at least there are no updates available from the vendor.
KeyDemon have some interesting products on their website, which I would love to get my hands on and play with, they are all in the image gallery that follows.
KeyGrabber Module - This one is interesting, you can take apart the target's keyboard and wire this inside, its just the 4 USB wires that you will be splicing this into, so easy peasy and ingenious! Providing it does not lock up and hang, this could be a good one.
VideoLogger - This looks like a HDMI, VGA or DVI connector, but they have some flash memory in the cable head which can capture images from the screen. Again, I would really like to have a play with this as I would be intregued as to how they do it, there is not a lot of space in there for a cpu, it may even be some tiny FPGA chip, who knows.
Key Grabber Forensic USB - Now this is what I should have bought, its a simple USB extension cable which won't look out of place if connected to the target computer, in fact, its a lot less suspicious than the KeyGrabber that I'm reviewing here.
KeyGrabber USB Keyboard - This is possibly the daddy of all of their keylogging products, why faff about with adapters or cables, when you can get a complete keyboard (albeit sh*tty quality) which has all of the functions built into it out of the box.
Scoring & Awards:
| Category | Score (1-10) | |
|
Installation |
Not Applicable | |
| Ease of Use | 8 | |
| Features | 6 | |
| Stability | 0 | |
| Ease of Update | Not Applicable | |
| Value for Money | 5 | |
| Licencing Fairness | Not Applicable | |
| Support/Warranty | 0 |
Overall Score = 4.5 out of 10
- About as stable as a potters wheel connected to a V8 Hemi.
- Super cheap, but unreliable.
- Unresponsive buttons in the GUI.
- Timestamps not recorded properly without an internet connection.
- Good luck with any warranty claims or support requests.
Competition closing date 10th October 2019
Comments:
Feel free to leave a comment, please note that all comments are moderated and won't appear here unless they are deemed appropriate (to keep the loonies out!).